Last February, I told you about the implementation of DMARC. In this second article, we will see what is behind a DMARC report through some questions. The aim of this series of articles is to help you - if you haven't already done so - to better protect your domain names with DMARC!
DMARC in three bullet points...
I'll make it short and simple: "DMARC" is an e-mail authentication standard that will rely on SPF & DKIM records. It will allow any advertiser who implements it to :
- Enforce SPF & DKIM limitations by applying a security rule in case of SPF & DKIM failure on the sending domain.
- Limit spam and phishing on your entire infrastructure (main domain & subdomains) thanks to reports provided by various organizations.
- Make all e-mail flows compliant to improve their legitimacy.
The only constraint of DMARC today is that all the organizations (Fai, Webmails, Anti-Spam Filters, etc.) do not interpret it!
A DMARC report... What is it?
First of all, to receive DMARC reports, you will have to configure an e-mail address in the "rua" tag.
v=DMARC1; p=none; rua=mailto:zc1cbjad@ag.dmarcian.eu, mailto:dmarc_agg@dmarc.250ok.net,mailto:dmarc_agg@lepatron.email;
Note: If you want to receive all the reports, you will have to choose an e-mail address of your sending domain (e.g. dmarc-rua@badsender.com for the domain name badsender.com). Otherwise, you will need to create a DMARC record (v=DMARC1;) on the domain external to your sending domain.
Once DMARC is in place, you will receive (depending on your settings), the activity results recorded on your sender domain. By this I mean the authentication results of your email campaigns but also third party activities - both legitimate and malicious.
This DMARC report is sent in ARF format (see attached). The file will be zipped and will contain the report in XML format.
Who sends these DMARC reports?
As I said before, the reports are sent by any organization that knows how to interpret DMARC and is able to send these famous reports.
Here is a list (not exhaustive) of the organizations for which we have received a report since January 1, 2021 (on 2 monitored domains):
| Organization | Organization | Zip format |
| ADP | Software | .GZ |
| Belgacom | Host | .GZ |
| BNP Paribas | Bank | .GZ |
| BPCE | Bank | .GZ |
| Caisse des Dépôts | Finance | .GZ |
| Cisco | Security | .GZ |
| Diennea | Technologies | .ZIP |
| Webmail | .ZIP | |
| Casino Group | Distribution | .GZ |
| Infomaniak | Host | .ZIP |
| La Poste | Webmail | .GZ |
| Social | .GZ | |
| Mail.ru | Webmail | .GZ |
| OC3 Network | Host | .GZ |
| Panalpina | Logistics | .GZ |
| Rackspace | Host | .ZIP |
| Sfr | Webmail | .GZ |
| Spamtitan | Security | .GZ |
| Strasbourg.eu | Community | .GZ |
| Telus | Telecommunications | .GZ |
| Yahoo | Webmail | .GZ |
| Zerospam | Security | .GZ |
| Zoho | Host | .GZ |
As you can see, the panel of companies is large and this is only a small proportion of what there may be as an organization returning DMARC-related information.
A DMARC report from the inside!!!
It's all very well to give you a lot of information about DMARC but I forgot the main thing... What information can be found in these famous reports ???
I'm going to break down a DMARC report we received from Gmail:
Structure of a report
A DMARC report is a file XML. You will find in this metadata all the authentication information related to your sender domain (and subdomains if it is placed on the root domain). This file is divided into 3 main sections:
- report_metadata" tag
- policy_published" tag
- Record" tag.
The "record" tag is the most important since it will contain all the authentication results. 1 record = 1 result, so the more records you have in your file, the more authentication results you will have to analyze! If you are a big sender, I strongly advise you to use a DMARC monitoring solution.
*spoil* >> I'm planning several articles in June about different solutions... But shhhh!
The "report_metadata" tag
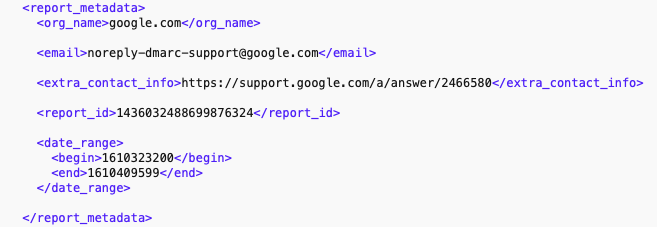
In this first section, you will find all the information related to the DMARC report:
- : The organization that provides the DMARC report.
- : The email address that sends the DMARC report.
- : A link to the support page on DMARC.
- : The ID of the DMARC report.
- : The analysis period of the report. In our example (once transformed), the analysis period is from 11/01/2021 00:00 to 11/01/2021 23:59 GMT.
The "policy_published" tag

In this second section, you will find all the information related to your DMARC policy:
- : Indicates the name of the domain (or subdomain) where DMARC is placed.
- : Indicates DKIM alignment => "r" (relaxed=soft) & "s" (strict=strict).
- : Indicates SPF alignment => "r" (relaxed=soft) & "s" (strict=strict).
- <p> Indicates the DMARC policy of the domain where "p" is set => "none" (i.e. no action), "quarantine" (i.e. put in spam), reject (i.e. e-mail blocked).
- : Indicates the DMARC policy of the subdomains of the domain where "p" is set => "none" (cf. no action), "quarantine" (cf. put in spam), reject (cf. blocked email).
- : Specifies the percentage of emails on which the DMARC rule should apply.
The "record" tag
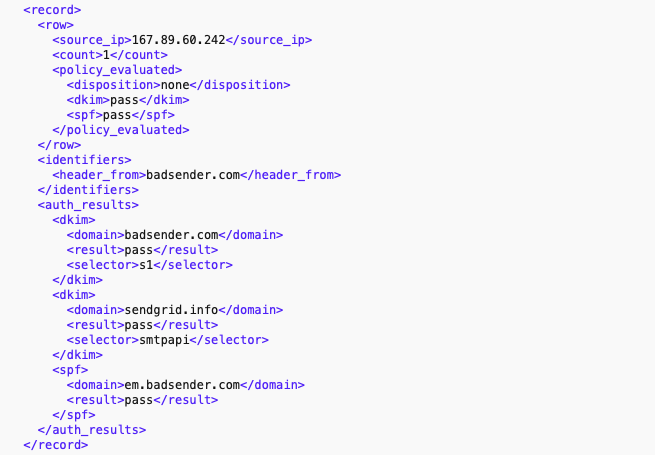
In this third section, you will find all the information related to the authentication results. This section is divided into three sub-sections:
- : Indicates the IP that was used to send the email.
- : Indicates the number of emails received with this IP.
- : Indicates the DMARC policy.
- : Indicates the authentication result for DKIM.
- : Indicates the authentication result for SPF.
: Indicates the domain that is used in the sending address.
- : Indicates the domain signed with DKIM.
- : Indicates the DKIM authentication result.
- : Indicates the selector for the DKIM key.
- : Indicates the domain signed with SPF.
- : Indicates the SPF authentication result.
Note: It is possible (as in the example) that a sending domain has multiple DKIM keys. Note that all DKIM keys will then be parsed in the subsection.
Conclusion...
That's it, the appetizer is over. The objective here was really to show you the inside of a DMARC report (done) before diving directly into the heart of DMARC, namely the data analysis.
So, we will see in the next article how to interpret DMARC report data! You'll see, it's super exciting... Or not 😉
Need help deploying DMARC? Find the most suitable DMARC monitoring solution? Monitor your DMARC data? Do not hesitate to contact us...
—–
Our latest content on DMARC :
- 16/05/2021 : Monito 2021 #05 | Monitoring DMARC Badsender.com - April 2021
- 09/04/2021 : Monito 2021 #04 | Monitoring DMARC Badsender.com - March 2021
- 05/03/2021 : Monito 2021 #03 | Monitoring DMARC Badsender.com - February 2021
- 12/02/2021 : Tech 2021 #01 | What if you deploy DMARC in 2021 on your domain name?
- 05/02/2021 : Monito 2021 #02 | Monitoring DMARC Badsender.com - January 2021
- 08/01/2021 : Monito 2021 #01 | Monitoring DMARC Badsender.com - December 2020
And on other email authentication systems:
- 12/10/2020 : What is DKIM? Configuration, verification and monitoring.
- 27/08/2020 : 10 tips to implement in your SPF configuration... ?
- 30/07/2020 : What is SPF? Configuration, verification and monitoring.
5 réponses
Hello, it's very interesting but could you explain if in an xml file received the record could indicate that a person (identifiable by his IP) has simply requested an online form that uses the MAIL function (php for example) or the SMTP parameters of our server?
Hello Alex,
DMARC reports only contain data from domains/subdomains where the DMARC record is placed, regardless of the system used to send the emails (outlook client, an Email Service Provider, an online form, etc.). Unfortunately, the IP you would retrieve is the IP of the form (not the IP of the person) provided that your domain/subdomain is set to the said form. If you want to retrieve the person's IP, you would have to record the information at the time they submit the form.
Kind regards,
Sebastien.
Hi,
Thanks for your informative article.
I need some help with DMARC reports. Though my SPF record lists the correct IP addresses, the under policy_evlauated is always coming as failed.
For example:
104.160.64.86
1
none
pass
fail
I've included ip4:104.160.64.86 in my spf record, but still the reports show it as "fail".
Would you have any idea why this happens?
Regards,
Sunil
Hi,
**The tags disappeared in my previous message, so I am repeating it here with the tag details**
I need some help with DMARC reports. Though my SPF record lists the correct IP addresses, the under policy_evlauated is always coming as failed.
For example:
[source_ip] 34.195.253.204 [/source_ip]
[count] 1 [/count]
[policy_evaluated]
[disposition] none [/disposition]
[dkim] pass [/dkim]
[spf] fail [/spf]
[/policy_evaluated]
I've included ip4:104.160.64.86 in my spf record, but still the reports show it as "fail".
Would you have any idea why this happens? I've done lots of searches but I could find no information on why this is happening.
Regards,
Sunil
Hello Sunil,
To respect the DMARC compliance, you need to have: A SPF record (based on your return-path domain) must be valid and aligned with your sender domain or a DKIM record (based on your domain signed d=) must be valid and aligned with your sender domain. If you don't respect this, the DMARC policy will apply!
If your DMARC compliance is fail, you could verify if your alignments are correct.
Example: If your sender domain is badsender.com, your SPF domain - to be valid and aligned - must be badsender.com or a sub-domain of badsender.com. For DKIM, this is the same way: if your sender domain is badsender.com, your DKIM signature - to be valid and aligned - must be made in badsender.com or a sub-domain of badsender.com
The majority of DMARC compliance issues come from forgetting an IP or misaligned domains.
Cheers,
Sebastien.