
If you follow the deliverability news very closely, you may know that several months ago, Microsoft launched a big merger/combination operation between the Outlook.com (now Hotmail) and Office365 infrastructures. Basically, and to caricature, everyone is migrating to Exchange Online. In reality, it's not that simple, there are still a lot of differences between the two in terms of email processing. But as usual, you shouldn't count on them to give us too many details, and that's quite normal.
What is X-Forefront-Antispam-Report?
For the record, Forefront was a family of security software published by Microsoft. At the email level, "Forefront Protect for Exchange Server" consisted in redirecting email traffic to a specialized Microsoft server in order to analyze it and send the final result to the user. After analyzing the emails, Forefront added some headers to the email, including the famous X-Forefront-Antispam-Report, so that when the email was received, the company (or Exchange in fact) would know what to do with the email, i.e. deliver it, block it or send it as spam (among other things).
In 2013, Forefront Protect for Exchange Server (FOPE) was renamed Exchange Online Protection (EOP) by Microsoft. Of course, renaming the technical headers of emails without seriously compromising backward compatibility is out of the question, which is why X-Forefront-Antispam-Report is still rampant.
How to find this technical header?
This is the starting point. If you suspect a problem with Office365 or Outlook/Hotmail, you will want to find the information contained in X-Forefront-Antispam-Report. But unfortunately you don't have access to your recipient's spam box, so you won't be able to easily check what happened to them. You will have to send a test email to an email box using this system, either an online Office365 account, or a Hotmail account, or obviously your company email if it is connected to Exchange which itself uses EOP (which is not necessarily the case). Be careful also that not all X-Forefront-Antispam-Report are the same, the filters configured on Hotmail are not necessarily configured with the same settings as those of Office365 or your company.
But never mind, here is how to display this information.
In Outlook.com/Hotmail.com and Office365
First, open your email and click on the downward pointing arrow next to the "Reply" button. Then select "View Message Source".

Then, a window will appear with all the lines of the technical header of your email, you will have to find the line starting with X-Forefront-Antispam-Report.
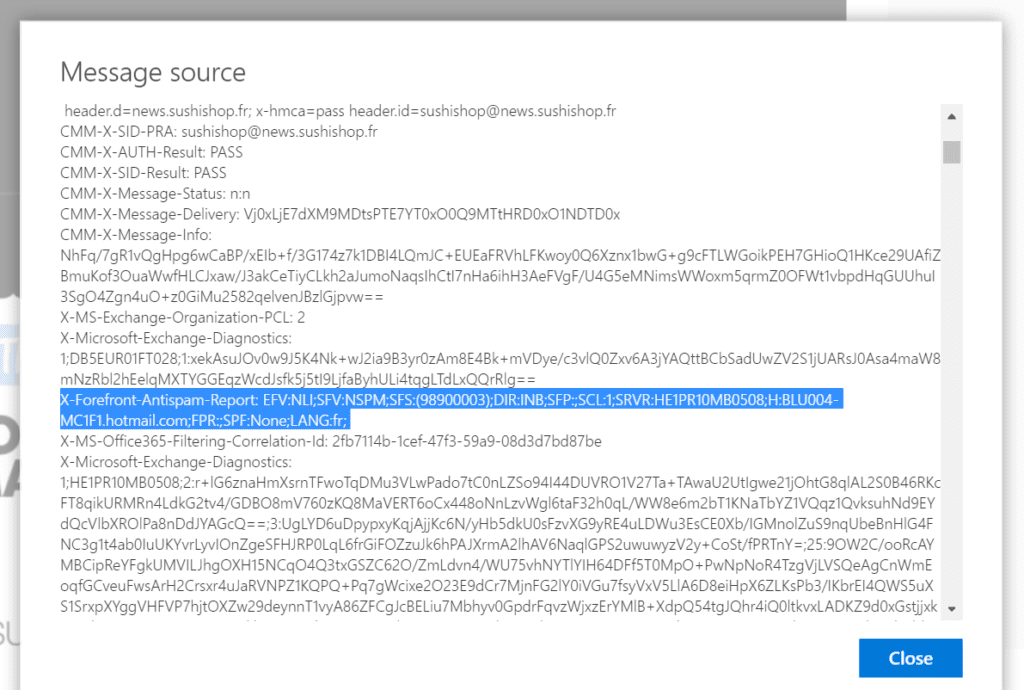
It goes something like this:
X-Forefront-Antispam-Report: EFV:NLI;SFV:NSPM;SFS:(98900003);DIR:INB;SFP:;SCL:1;SRVR:HE1PR10MB0508;H:BLU004-MC1F1.hotmail.com;FPR:;SPF:None;LANG:fr;Need help?
Reading content isn't everything. The best way is to talk to us.
In Outlook Desktop
Open the email in a dedicated window and click on "File" and then on the "Property" button
Then, in the window that appears, you will have to find the line beginning with X-Forefront-Antispam-Report.
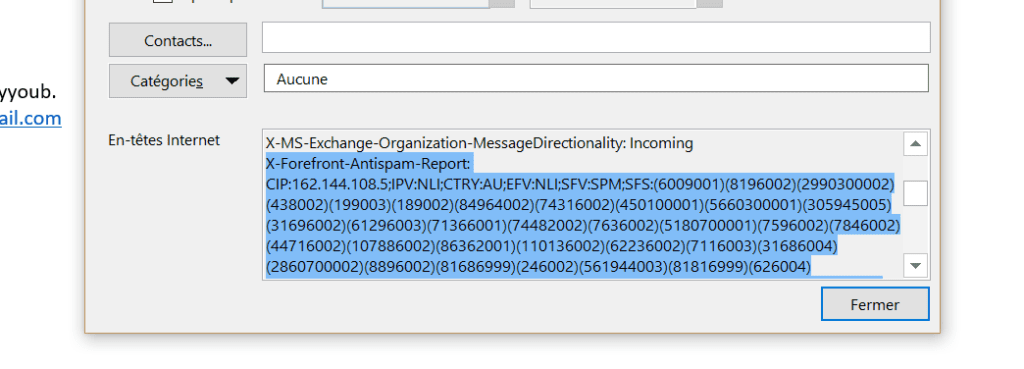
In this second case, it gives this (there is more to say than in the previous example:
X-Forefront-Antispam-Report: CIP:162.144.108.5;IPV:NLI;CTRY:AU;EFV:NLI;SFV:SPM;SFS:(6009001)(8196002)(2990300002)(438002)(199003)(189002)(84964002)(74316002)(450100001)(5660300001)(305945005)(31696002)(61296003)(71366001)(74482002)(7636002)(5180700001)(7596002)(7846002)(44716002)(107886002)(86362001)(110136002)(62236002)(7116003)(31686004)(2860700002)(8896002)(81686999)(246002)(561944003)(81816999)(626004)(3480700004)(1096003)(104016004)(356003)(956001)(50986999)(35302002)(8676002)(4001450100002)(53806999)(109986004)(93156004)(50226002)(45086001)(23686003)(106466001)(93146003)(230700001)(9686002)(33646002)(586003)(47776003)(4001600100001)(19580395003)(881003)(229853001)(9786002)(189998001)(19580405001)(50466002)(1671002)(43066003)(2700400007);DIR:INB;SFP:;SCL:5;SRVR:AM4PR0101MB1682;H:server.serverhof.com;FPR:;SPF:Pass;PTR:server.serverhof.com;A:1;MX:1;LANG:en;How to interpret X-Forefront-Antispam-Report?
This is obviously what you are most interested in, and the basis of this article. Microsoft has very generously provided us with documentation that you can find here or by continuing to read this article.
In the examples given above, we see that X-Forefront-Antispam-Report is a sequence of information separated by semicolons. Each piece of information will give us an indication of how the Microsoft spam filter perceived the email:
- CIP: The IP address of the connection
- CTRY : The country of origin of the message
- LANG : The language of the email as specified at the time of sending
- SCL: This is the "Spam Confidence Level", it is a very important notion. It is in fact a score that goes from -1 to 9:
- from -1 to 1 the emails are destined to the inbox (-1 is in fact a whitelisted sender)
- from 5 to 6 the email is suspected to be a spam and will be delivered in spam box
- from 7 to 9 the email is considered as spam and will be delivered in spam box
- Note: the scores 2, 3, 4, 7 and 8 are never given by the system, except in exceptional cases, you should not find it
- PCL: This is the "Phishing Confidence Level:
- from 0 to 3 the email is not considered as phishing
- from 4 to 8 the email is considered as phishing
- -9990 email is considered as phishing
- SRV: If the value is set to "Bulk", this means that EOP considers the email to be a mass message. This is not necessarily a bad thing, unless an administrator has decided that all bulk messages should be considered spam.
- SFV: This is probably the most interesting indicationSince it explains why the message ended up where it did, here are the different possible values:
- SFE: Filters have been bypassed because the sender is registered in the recipient's Safelist
- BLK: The filters have been bypassed and the message has been blocked because the sender is in the recipient's blocklist
- SPM: The message has been branded as spam by the content filter
- SKS: The message was marked as spam before it passed through the content filter
- SKA: Filters have been bypassed and the message delivered to the inbox because the sender is in a spam filter's allowed sender list
- SKB: The message has been marked as spam because the sender is referenced in a block list of the spam filter
- SKN: The message was marked as not spam before it passed through the content filter. For example because a specific rule has been defined.
- SKI : Like SKN
- SKQ: The message has been released from quarantine and has been sent to the recipients
- NSPM: The message has been marked as not spam and has been sent to the recipients
- IPV : Defines if a message element (IP, domain, sender, ...) is in an authorized list (CAL value) or if it is not in a reputation list (NLI value)
- H: HELO or EHLO string of the connection server
- PTR: Gives the reverse DNS
Be careful, all this information is not always present in all emails. Moreover, if we look mainly at the value of "SFV", we quickly realize that it is difficult to simulate what happened on the specific configuration of your recipients (especially in B2B).
Need to move forward on email deliverability issues? Discover our deliverability services
Leave a Reply