Imagine that your phone rings. On the screen, the number of your best friend appears. You take your phone in hand, pick it up and put it to your ear. There, to your surprise, it's not your best friend saying hello... but the smooth voice of a commercial phone server offering to buy the latest model of an appliance you don't need.
Impossible you may say! Indeed, with your phone, unless you face a very ingenious hacker, it is impossible. On the other hand, when it comes to email, nothing could be simpler: you can send an email on behalf of barack@whitehouse.gov to all your friends. Or rather, you could. In fact, basically the SMTP protocol does not provide an authentication mechanism: anyone can send an email on behalf of... anyone!
Obviously, with the increase in the number of emails sent, and especially the number of spam (and other phishing), a solution had to be found. It is in the early 2000s that discussions are engaged, which will lead to the publication in 2006 of SPF and the following year of DKIM. And the need to ensure the authentication of emails.
Email authentication and SPF = Sender Policy Framework.
Unfortunately, we won't be able to continue with our example of the phone call... the analogy would be too shaky 🙂
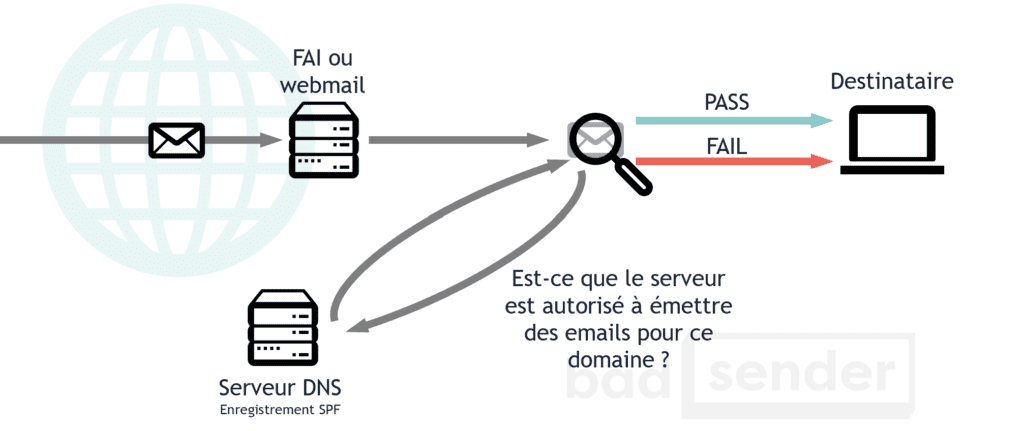
When sending an email, the main source of identification of the sender is the email address contained in the FROM: field. This email address consists of two parts: the part to the right of the "@" sign, the domain name, and the part to the left, the user name. SPF is a technique that will define which servers have the right to send an email for the domain name (i.e. the right part of the address).
Let's take for example... "example.net". Example.net is a big online payment site. And so, they don't really want anyone to try to impersonate them, it's bad for their reputation. So they decided to publish an SPF record on their DNS server, here is what it looks like (this is an example, everything is fictitious):
example.net. IN TXT "v=spf1 ip4:192.0.2.0/24 ip4:198.51.100.123 a -all" example.net. IN SPF "v=spf1 ip4:192.0.2.0/24 ip4:198.51.100.123 a -all"
Here we have two similar DNS records: one is of type SPF and the other is of type TXT for backward compatibility. What do these records mean? That servers with IP address 198.51.100.123 and all IP addresses in the 192.0.2.0/24 block are allowed to send emails on behalf of Example.net. The "a" means that all IP addresses of the A record are also allowed to send emails for this domain name. The "-all" means that all other IPs must be rejected ("SPF=FAIL").
Need help?
Reading content isn't everything. The best way is to talk to us.
But beware, an email that does not pass the SPF test will not be considered as SPAM. On the other hand, a domain name with a well-configured SPF record will be less likely to be exploited by spammers.
Email authentication and DKIM = DomainKeys Identified Mail.
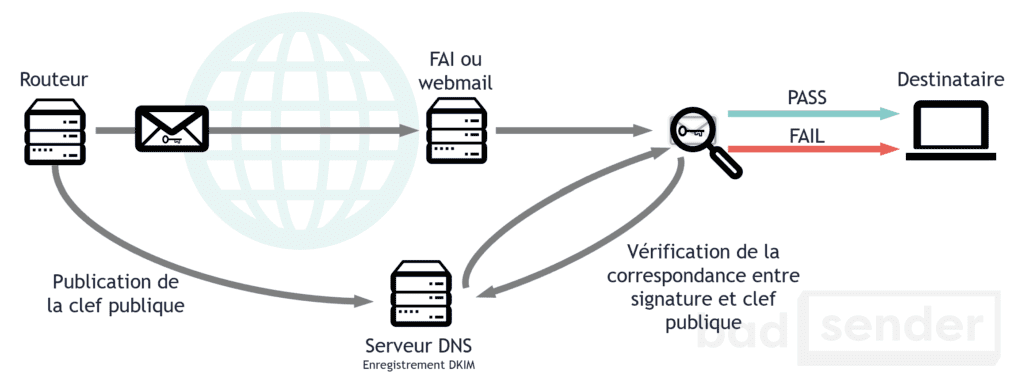
DKIM is the fusion of two technologies, one developed by Yahoo! (DomainKeys) and the other developed by Cisco (Identified Internet Mail). Where SPF tries to link a domain name to the IP address sending the message, DKIM tries to associate a domain name to a message by adding a digital signature. The verification of the signature is done via a key located in a DNS record. In doing so, DKIM can verify whether a message has been tampered with during its transport between different SMTP servers. And it guarantees that the content will arrive intact to the recipient.
Like SPF, DKIM does not prevent SPAM. But it does allow it to be seen as more legitimate by the servers receiving the messages. Filters can then focus on unsigned messages and filter them more aggressively.
Example of a DKIM signature contained in the header of an email:
DKIM-Signature: v=1; a=rsa-sha256; d=example.net; s=brisbane;
c=relaxed/simple; q=dns/txt; l=1234; t=1117574938; x=1118006938;
h=from:to:subject:date:keywords;
bh=MTIzNDU2Nzg5MDEyMzQ1Njc4OTAxMjM0NTY3ODkwMTI=;
b=dzdVyOfAKCdLXdJOc9G2q8LoXSlEniSbav+yuU4zGeeruD00lszZ
VoG4ZHRNiYzR
Email Authentication and DMARC = Domain-based Message Authentication, Reporting and Conformance.
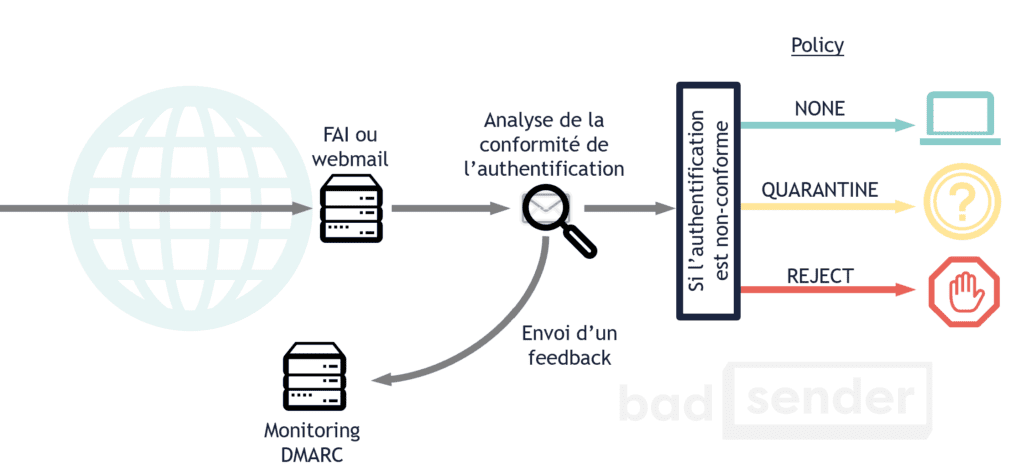
DMARC plays on the synthesis between SPF and DKIM. Not by replacing them, but by uniting them. And by making them more intelligent. There are two main uses of DMARC:
- Indicate what the ISP/Webmail should do with the message if the authentication fails (let it through, delete it, classify it as spam, ...).
- Allow the sender to be notified when authentication fails.
DMARC has been designed by several big names in the email industry (Return Path, Gmail, AOL, Microsoft, ...) in order to fight more effectively against phishing attacks, which are on the rise. This is why companies such as Paypal, Facebook or LinkedIn have also joined this initiative.
Note.
I am well aware that the subject of email authentication is very technical. So don't hesitate to ask for more details in the comments, I'll be happy to answer them. Moreover, I will probably come back in more detail on these different technologies in the future.
24 réponses
One of the most frustrating aspects of DMARC is that although it is quite constraining to set up, its efficiency is quite relative. Certainly, it becomes impossible to send a From mail: service@maboite.com if DMARC is correctly configured for this domain, but service@maboi1e.com has no restrictions. Worse, the owner of the domain could even quietly configure his SPF, DKIM and DMARC, while pretending to be someone else in the eyes of the uninformed.
Moreover, if it is true that domains using SPF and DKIM are generally well seen by the receiving ISPs, it is not the case for DMARC whose approach is voluntarily neutral.
Finally, DKIM, in addition to guaranteeing the integrity and non-alteration of a message by a third party, allows receiving ISPs to create a reputation for each domain signing in DKIM, since the sender is necessarily who he claims to be. If he is sending spam, he is himself, and the ISP will ruin his reputation. If they are clean, the reputation of the domain will increase and the sending quotas will eventually increase.
It's always good to review the classics and popularize them.
Dmarc is indeed very important for sensitive sites/domains or companies, even if I think that eventually everyone will use it by default.
Benjamin,
Thank you for your comment (and sorry, it didn't get published right away because it was pending approval).
Concerning your remark about DMARC, unfortunately, few solutions allow to really fight against phishing and it is obviously possible to be the biggest spammer in the world and to have valid emails at SPF, DKIM, DMARC and c° level.
But to fight against maboi1e.com, I see very few solutions, especially if we stay with our good old SMTP (which still has a good day ahead of it).
See you soon,
WELL, this delay between my comment and its publication is quite timely since I am currently working on a project that will attempt to humbly address this very problem.
More info when it will be official =)
Can't wait to hear more 😉
Hello,
So far, no problem with receiving my newsletter.
Since a few days, my newsletter is rejected, on an address in aol.com, with the Diagnostic-Code: smtp; 521 5.2.1
No problem with other shipping addresses.
What can I do to get my newsletter back to its recipient?
Hello,
Is there a way on gmail to ask for an identification of those who send the emails, or for example to accept emails that are certified and recognized IP address?
Because I get about 20 spam and fishing emails a day from the same hacker, who was a friend a long time ago.
I know who he is, but I can't prove it because he sends me all kinds of emails.
So I would like to know if there is a software or an option in gmail, which obliges those who send me emails to have trackable IP addresses?
for my question on DKIM: for the configuration or header that are passed with the config of dkim?? and 2question for spf: is there any application that makes to check 150000000 milion domian?? and mrc in advance
Anthony > To my knowledge, there is no such option in Gmail. I'm sorry.
Karim > Sorry, but I don't understand your questions.
Hello Jonathan and thank you for your very interesting article.
At ease with setting up websites, I don't know anything about email protection, I understand php but I don't program, I get assistance.
Anyway, for a long time now, I've been getting email returns that I don't send with email addresses from my NDD that don't exist.
Would DMARK be a plus against this practice of usurpation and if so, can you be precise when: where and what to put in place on my server. Reading you, I imagine that it is a simple text file to put at the root of its www ? What would be the line of code to put in it?
I thank you very much because for people like me, it is difficult to find a "ready-made code"...
Julien 🙂
all this is good but it's been a year that I'm fighting with illicit messages, I block the sender, I report as pishing, I warn google I try to find sites of alert, finally all that unimaginable to this day I always receive and always the same but each time the addresses changed
So I would like to find a solution to stop all this. Thank you for helping me Patricia
Solutions exist to close the door to spam but they are not suitable for everyone, but for a lamba user, it is usable without problem.
If you have your own domain (@dupont.fr) and access to a panel similar to cPanel, you can :
- Enable Greylisting, in short your server makes the sending server wait, if it's spam, it won't be returned.
- Activate BoxTrapper, a sender whose email is not in your whitelist, has to answer a verification manually at his first sending. Then his other emails will be accepted without confirmation.
If you don't have your own domain, you can use a third party filtering service, some of which are free like spamfence.net.
You can also use temporary, semi-temporary or dedicated emails.
A bit long to explain... I am preparing various articles on protection in general.
Keep on with the emails and let the telephony do its thing 😉
Contrary to your first paragraph, it is very easy to display a name and number with IP telephony, because most providers let the callerID sent by your PBX pass through without filtering. By this very fact I can call someone by displaying the name and number of the police station of the neighborhood without problem.
So be careful
Have a nice day
Eric Beaulieu
VoIP specialist, void in email 😉
Not a very nice comment Eric, did you have a bad day?
We're on an emailing blog, in a 2014 post you dug up and you come along and bring it back with technical elements about IP telephony to point out the inaccuracy of an image Jonathan used to illustrate his point about identification and authentication needs and methods in emailing.
Nothing to add, we have a perfect! You made my day 🙂
Good morning,
thank you for the explanations.
Indeed, it is very technical and well detailed.
Sincerely
Hello,
I was wondering if it is possible to not have all our emails signed DKIM. In a few words to explain: my emails can be sent by 3 different servers, if I set up DKIM on the DNS record, does the encryption have to be set up on all 3 servers?
Thanks for the feedback 😉
Nicolas
Hello,
In the ipv4 field of the SPF, can I indicate a domain name such as "nom.fr" instead of putting directly an IP / IP range?
@Rr0ty
Yes and no 😉 a domain name alone has no interest, since SPF always requires IP addresses, they are the ones we authenticate. On the other hand it is possible to use the "include:domain.com" mechanism to use the IPs declared in the SPF record of another domain. It is also possible to designate the IPs of the MX and A records.
We should have a little update of the article to dig into these different points!
Goodour
Thank you for this article.
Can we declare SPF, DKIM and DMARK records in our own external DNS server (e.g. ns1.mondomaine.com) or do we have to ask our ISP to put them on their public DNS?
Thank you in advance.
Hello,
First of all very good and educational article.
I take the liberty of updating the question of "Nicolas 08/01/2019": is it necessary to configure DKIM on all the servers (MX & SPF)?
Thank you for your answers.
Hello to all.
I agree with Jonathan's answer (thanks again):
Hello Hamid,
Yes, it is necessary to configure/sign with DKIM all emails, whether they come directly from your corporate email server (the one in your MX mailbox) or from a hosting company. Without DKIM, you are very likely to get spam.
Your SaaS host must provide you with other DKIM keys to place in your DNS.
Kind regards,
Jonathan
@+
Hello again,
I would like to ask another question, still on the subject of DKIM/SPF/DMARK: what are the prerequisites to do mass mailing (several thousand recipients) without being blacklisted ...?
Thank you in advance for your answers and time.
à+,
Zine
Good article.
To complete: How to analyze your DMARC reports?
https://www.dmarc.fr/blog/comment-analyser-vos-rapports-dmarc
Have a nice day,